Are you losing your advertising budget to click fraud? You’re not alone. Studies show that up to 27% of all online ad clicks may be fraudulent, costing businesses billions annually. ClickMoat’s advanced protection system helps you fight back by identifying and blocking suspicious clicking patterns before they drain your ad spend.
In this comprehensive guide, we’ll walk you through setting up and optimizing ClickMoat’s protection features to maximize your ROI and ensure your ads reach real, potential customers.
Understanding Click Fraud Protection
What is Click Fraud?
Click fraud occurs when individuals or bots repeatedly click on your ads with no intention of becoming customers. This malicious activity can quickly deplete your advertising budget and skew your marketing metrics.
How ClickMoat Protects Your Ads
ClickMoat employs a multi-layered approach to protect your ads:
- Real-time click pattern analysis
- IP-based fraud detection
- Device fingerprinting
- Machine learning algorithms
- VPN detection and blocking
Click Fraud Threshold Rules
ClickMoat’s threshold system allows you to create up to 5 customized rules to catch different types of fraudulent behavior. Here’s how to set them up effectively:
Rule 1: Quick Fraud Detection (5-Minute Window)
Why This Matters:
- Stops aggressive click fraud attempts
- Prevents rapid-fire automated clicks
- Protects against immediate budget drain
Implementation Tips:
- Start with 2 clicks per 5 minutes
- Monitor false positives for the first week
- Adjust based on your average user behaviour
Rule 2: Hourly Protection (60-Minute Window)
Why This Matters:
- Catches distributed clicking patterns
- Identifies manual click fraud attempts
- Balances protection and user experience
Best Practices:
- Review your Google Analytics time-on-site metrics
- Consider peak business hours
- Adjust for different ad campaigns
Rule 3: Daily Monitoring
Why This Matters:
- Detects sustained fraudulent activities
- Protects daily ad budgets
- Identifies professional click fraudsters
Optimization Tips:
- Align with your daily ad spend
- Consider your sales cycle
- Account for business hours
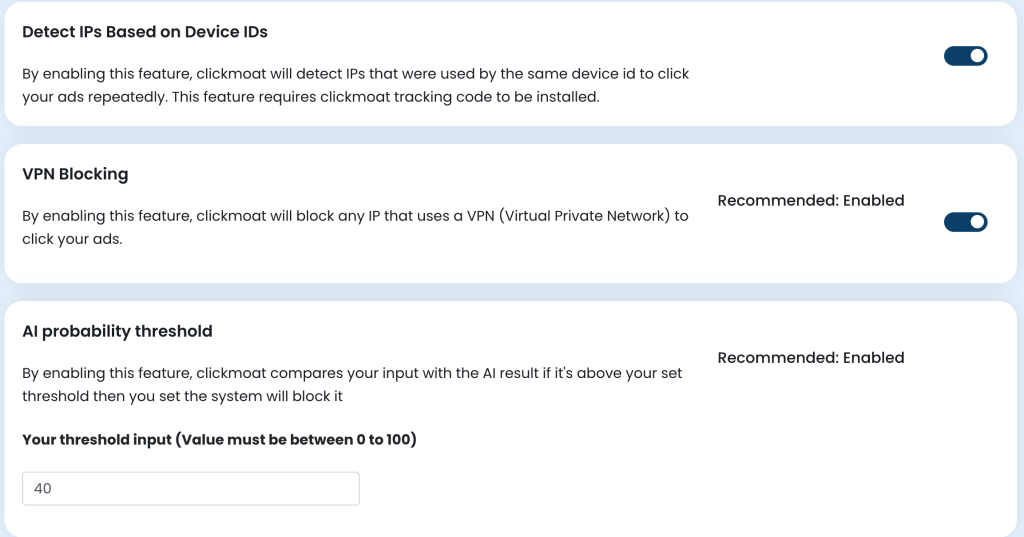
Device ID Detection
Purpose: Track suspicious activities across IP addresses using device fingerprinting.
Key Features:
- Cross-IP tracking
- Persistent fraud detection
- Device-level blocking
Setup Requirements:
- Enable in dashboard
- Set threshold sensitivity
VPN Protection
Why It’s Important:
- Blocks fraudulent VPN-based clicks
- Prevents geographic manipulation
- Reduces click farm access
Configuration Options:
- Enable/disable VPN blocking
- Set blocking sensitivity
- Whitelist trusted VPNs
AI Probability Threshold
Uses machine learning to analyze clicking patterns and assign risk scores.
Setting Up AI Protection:
- Enable the feature
- Set your threshold (0-100)
- Recommended starting point: 40
- Lower values = more strict
- Higher values = more lenient
Part 2: Auto IP Blocking System
The Real Cost of Not Using IP Blocking
Let’s look at a real scenario:
- Average Cost Per Click: $2
- Fraudulent Clicks Per Day: 50
- Daily Loss Without Protection: $100
- Monthly Loss: $3,000
With proper IP blocking, you can prevent these repeat offenders from draining your budget.
Understanding the IP Blocking System
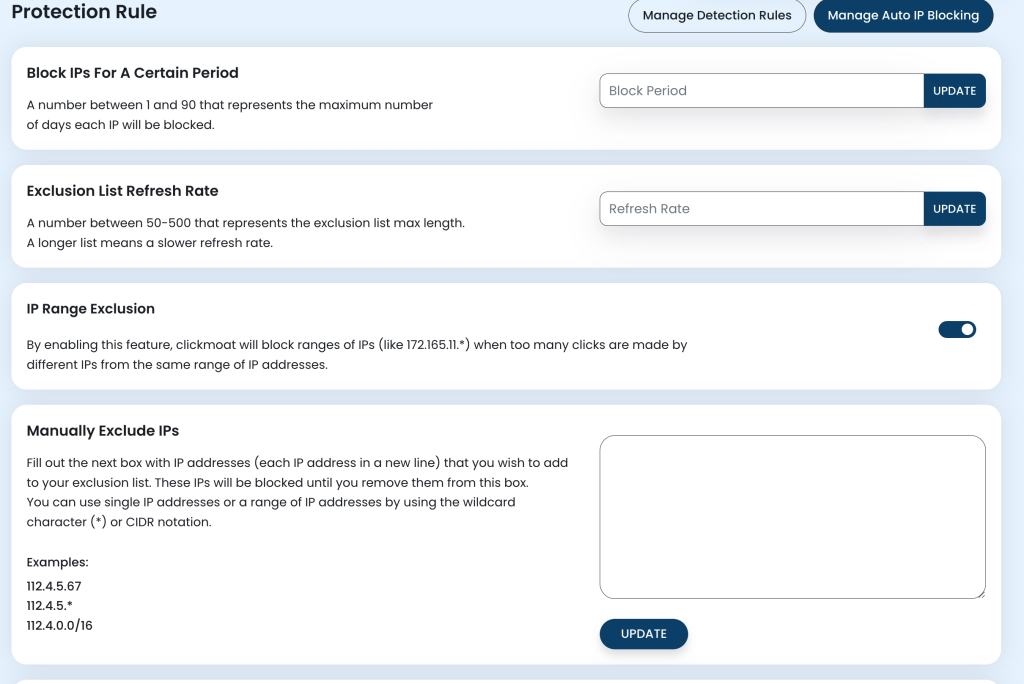
1. Block Period Configuration (1-90 Days)
Why Block Period Matters
- Prevents immediate return of fraudsters
- Creates a cooling-off period
- Builds a database of known bad actors
Optimal Block Periods by Industry
E-commerce:
- Recommended: 45-60 days
- Why: Balances protection with potential customer return
- Peak Season Adjustment: Consider reducing to 30 days during holidays
B2B Services:
- Recommended: 60-90 days
- Why: Higher CPC requires stricter protection
- Adjustment: Can be more aggressive due to lower natural click volume
Local Services:
- Recommended: 30-45 days
- Why: Allows for regular customer return visits
- Consideration: Adjust based on service frequency
Block Period Optimization Tips
- Start Conservative
- Begin with 30-day blocks
- Monitor blocked IP patterns
- Adjust based on fraud recurrence
- Monitor False Positives
- Keep track of whitelist requests
- Review geographic patterns
- Adjust for legitimate high-frequency users
- Seasonal Adjustments
- Reduce during high-traffic seasons
- Increase during low-activity periods
- Align with marketing campaigns
2. Exclusion List Management
Why Your Exclusion List is Critical
- Creates a strong defense perimeter
- Prevents known fraudsters from returning
- Reduces monitoring workload
List Size Optimization (50-500 IPs)
Small Business (50-100 IPs)
- Perfect for low-traffic sites
- Faster refresh rate
- More manageable monitoring
Medium Business (100-300 IPs)
- Balanced protection
- Moderate refresh rate
- Good for most businesses
Large Business (300-500 IPs)
- Comprehensive protection
- Slower refresh rate
- Best for high-traffic sites
Management Best Practices
- Regular List Cleanup
- Review monthly
- Remove outdated entries
- Update based on new patterns
- Documentation
- Record blocking reasons
- Track fraud patterns
- Note any impact on traffic
- Performance Monitoring
- Watch refresh rates
- Monitor system impact
- Balance list size with performance
3. IP Range Exclusion
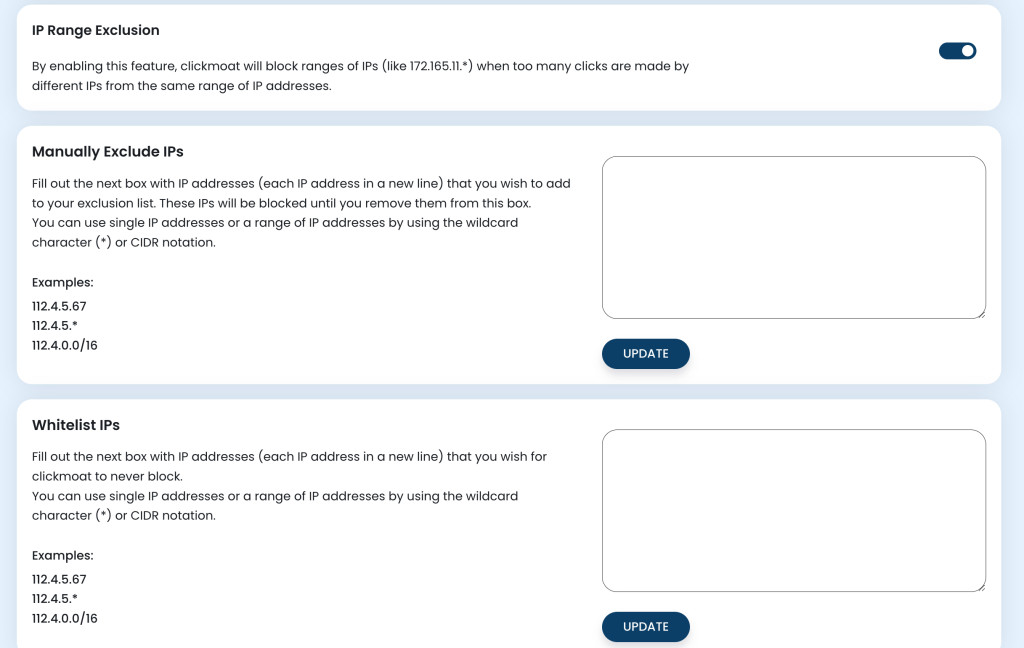
Why IP Range Blocking is Powerful
- Stops entire fraud networks
- Prevents IP-switching evasion
- More efficient than individual IP blocking
Real-World Applications
Click Farm Example:
Detected Pattern: 172.165.1.1 through 172.165.1.50 Solution: Block 172.165.1.* Result: Entire click farm operation blocked
VPN Network Example:
Detected Pattern: Multiple IPs from 185.193.x.x Solution: Block 185.193.0.0/16 Result: Entire VPN range blocked
Configuration Steps
- Enable Range Detection
- Turn on IP range monitoring
- Set pattern recognition threshold
- Configure alert system
- Set Trigger Conditions
- Number of IPs in range
- Time window for detection
- Suspicious activity threshold
- Monitor and Adjust
- Review blocked ranges
- Check for legitimate traffic impact
- Fine-tune range definitions
4. Manual IP Management
Why Manual Control Matters
- Immediate response to detected fraud
- Custom control over protection
- Ability to handle unique situations
Exclusion Methods
- Single IP Blocking CopyFormat: 112.4.5.67 Use: Specific fraudulent sources
- Wildcard Blocking CopyFormat: 112.4.5.* Use: Related IP groups
- CIDR Notation CopyFormat: 112.4.0.0/16 Use: Large network blocks
Whitelist Management
Why Whitelisting Matters
- Prevents false positives
- Allows legitimate high-frequency users
- Maintains business relationships
Essential Whitelist Entries
- Your Office IPs
- Client Networks
- Testing Systems
- Marketing Partners
Whitelist Best Practices
- Verify Each Entry
- Confirm legitimacy
- Document reason
- Set review date
- Regular Reviews
- Monthly verification
- Remove outdated entries
- Update as needed
Implementation Strategy
Week 1: Basic Setup
- Configure block periods
- Set up initial exclusion list
- Enable IP range blocking
- Create essential whitelists
Week 2: Monitoring
- Review blocked traffic
- Identify false positives
- Adjust block periods
- Fine-tune range detection
Week 3: Optimization
- Clean up exclusion lists
- Update whitelist entries
- Adjust range parameters
- Document effective patterns
Measuring Success
Key Metrics to Track
- Blocked IP Statistics
- Number of blocks
- Block duration effectiveness
- Range block impacts
- Cost Savings
- Prevented fraudulent clicks
- Saved ad spend
- ROI improvement
- System Performance
- Refresh rate impact
- False positive rate
- Detection accuracy
Troubleshooting Common Issues
Problem: High False Positive Rate
Solution:
- Review block periods
- Adjust range parameters
- Update whitelist
- Monitor legitimate traffic patterns
Problem: Persistent Fraud
Solution:
- Increase block periods
- Expand range blocking
- Review exclusion list
- Enhance monitoring
Best Practices Summary
- Regular Maintenance
- Weekly review of blocks
- Monthly list cleanup
- Quarterly strategy review
- Documentation
- Keep detailed records
- Track pattern changes
- Document decisions
- Continuous Optimization
- Monitor effectiveness
- Adjust parameters
- Update strategies
Conclusion
Effective IP blocking is crucial for protecting your ad spend. By properly configuring and maintaining your IP blocking settings, you create a robust defense against click fraud while ensuring legitimate users can still reach your ads.
Need help? Contact ClickMoat support for personalized IP blocking strategy assistance.